Master Social Engineering Techniques and Security Countermeasures for Enhanced Cybersecurity

In the ever-evolving digital landscape, cybersecurity has become paramount. Among the most prevalent and dangerous threats to data security are social engineering attacks. These sophisticated psychological manipulations aim to deceive individuals into divulging sensitive information, granting access to secure systems, or executing malicious actions.
To effectively combat social engineering attacks, it is essential to understand the techniques employed by attackers and implement robust security countermeasures. This comprehensive guidebook, 'Social Engineering Techniques and Security Countermeasures', provides an in-depth exploration of social engineering methods and equips readers with the knowledge and tools necessary to protect themselves and their organizations from these insidious threats.
4 out of 5
| Language | : | English |
| File size | : | 3451 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 264 pages |
Chapter 1: Demystifying Social Engineering Techniques
- Understanding the psychology behind social engineering
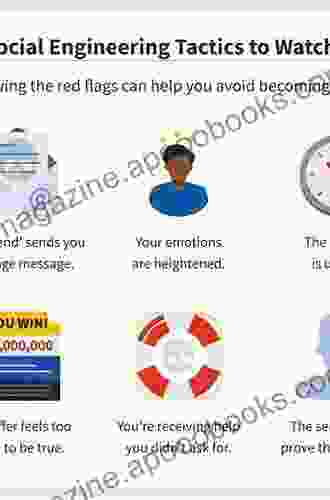
- Common social engineering attack vectors: phishing, spear phishing, vishing, smishing
- Identifying red flags and suspicious communication tactics
- Case studies of successful social engineering attacks
Chapter 2: Malware and Ransomware: The Grave Consequences of Social Engineering
- How social engineering attacks lead to malware and ransomware infections
- Types of malware and their impact on systems and data
- Ransomware attacks: tactics, consequences, and prevention strategies
- Best practices for malware and ransomware recovery
Chapter 3: Identity Theft and Data Breaches: The Devastating Impact of Social Engineering
- Social engineering techniques used for identity theft and data breaches
- Consequences of identity theft: financial loss, reputation damage, and emotional distress
- Data breaches: causes, types, and potential impact on businesses
- Best practices for preventing and mitigating identity theft and data breaches
Chapter 4: Security Countermeasures: Shielding Against Social Engineering Attacks
- Implementing strong passwords and two-factor authentication
- Educating employees on social engineering threats and best practices
- Deploying technical solutions: firewalls, intrusion detection systems, and email filters
- Developing incident response plans and conducting regular security audits
Chapter 5: Advanced Techniques and Future Trends in Social Engineering
- Emerging social engineering tactics: deepfakes, spear phishing 2.0, and social media manipulation
- Artificial intelligence: its role in social engineering and security countermeasures
- Future trends in social engineering and cybersecurity
- Best practices for staying ahead of the curve and protecting against evolving threats
In the relentless battle against cyber threats, 'Social Engineering Techniques and Security Countermeasures' serves as an indispensable weapon. By delving into the intricacies of social engineering attacks and providing practical security countermeasures, this guidebook empowers readers to protect themselves, their organizations, and the integrity of their digital assets.
With its comprehensive coverage, expert insights, and actionable advice, this book is an essential resource for cybersecurity professionals, IT administrators, business leaders, and anyone concerned about protecting themselves from the dangers of social engineering.
Testimonials


- CEO, Fortune 500 Company
Free Download Your Copy Today
Don't wait any longer to safeguard your digital assets and protect yourself from the growing threat of social engineering. Free Download your copy of 'Social Engineering Techniques and Security Countermeasures' today and gain the knowledge and tools to stay ahead of cybercriminals.
Free Download Now
4 out of 5
| Language | : | English |
| File size | : | 3451 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 264 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Thomas M Nichols
Thomas M Nichols Heidi Hayes Jacobs
Heidi Hayes Jacobs Morris Panych
Morris Panych Michaela Angemeer
Michaela Angemeer Ivy Pochoda
Ivy Pochoda Ian Mcnulty
Ian Mcnulty Roger Lowenstein
Roger Lowenstein Iantha Ussin
Iantha Ussin Holger Balodis
Holger Balodis Htebooks
Htebooks Helen Small
Helen Small Layla Knight
Layla Knight Rachel Louise Snyder
Rachel Louise Snyder J D Bartleson
J D Bartleson Harold L Cole
Harold L Cole Hayim Herring
Hayim Herring Scooter Tramp Scotty
Scooter Tramp Scotty Herbert Read
Herbert Read Kathleen Belew
Kathleen Belew Havelock Ellis
Havelock Ellis
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Francis TurnerThe Competition to Control World Communications, 1900-1945: A Historical...
Francis TurnerThe Competition to Control World Communications, 1900-1945: A Historical... Dustin RichardsonFollow ·16.6k
Dustin RichardsonFollow ·16.6k Isaiah PowellFollow ·19.1k
Isaiah PowellFollow ·19.1k William FaulknerFollow ·13.2k
William FaulknerFollow ·13.2k Alex FosterFollow ·13.5k
Alex FosterFollow ·13.5k Jason ReedFollow ·16.7k
Jason ReedFollow ·16.7k Michael CrichtonFollow ·4.5k
Michael CrichtonFollow ·4.5k Brady MitchellFollow ·14.3k
Brady MitchellFollow ·14.3k Bradley DixonFollow ·15.5k
Bradley DixonFollow ·15.5k

 Stanley Bell
Stanley BellUnlock the Secrets of Powerball Success: Master the...
Prepare to shatter the odds and transform...
 Ernest J. Gaines
Ernest J. GainesPatti Smith Horses 33 55: A Photographic Journey into a...
Journey into the raw and...

 Isaiah Price
Isaiah PriceMoyamoya Disease Diagnosis And Treatment: A Comprehensive...
Moyamoya Disease...

 Joseph Foster
Joseph FosterRecent Advances in Ophthalmology, Volume 14
Editor: [Editor's...
4 out of 5
| Language | : | English |
| File size | : | 3451 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 264 pages |